Secure Software Development
Unit work
Various pieces of work created throughout the units.
Scrum Security Review
“Some say that people are the biggest risk of cyber security”
Data protection and GDPR Compliance are essential to companies working with personal data, however employees or people within the workplace are a risk to the safety of this data. By managing people within the workplace data can be protected, 5 ways of protecting and managing using ISO/IEC Standard 27000 is policy, competence, audit, access control and authentication.
Access control ensures that employees cannot access areas or information they should not require to complete their job such as read/write access for areas of the company’s databases. Limiting access depending on job role inputs a level of structure and security to the company.
Authentication is another method that limits who can access data. This could be through login systems, physical doors or using protection such as multifactor authentication to limit how someone is authenticated. By guaranteeing who is accessing the data you have knowledge of who is a risk and can implement measures to protect data further.
Further control can be achieved by implementing policies. The use of policy within a workplace gives employees structure and understanding of what is required of the employee as well as the consequences of not following them.
Audits can support employees by informing them of ways they can improve as well as providing sufficient data to the employer of who is competent in data security and who requires further training.
Overall, people within a company are the biggest risk of cyber security when they are not trained and managed correctly following the ISO/IEC Standard 27000.
References:
iso.org (2021) ISO/IEC 27000:2019. Available at: https://www.iso.org/obp/ui/#iso:std:iso-iec:27000:ed-5:v1:fr (Accessed: 01 September 2022).
Pillai, A. B. (2017) Software Architecture with Python.
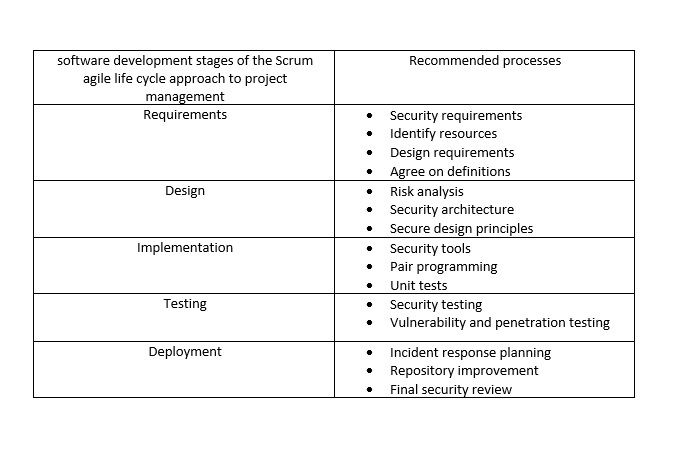
Scrum Agile table
Cyclomatic Complexity's
Cyclomatic complexity is a measurement developed by Thomas McCabe. It was created to determine the stability and confidence level of a code by determining the complexity of it by counting the number of linear paths within the code. (IBM , 2021) The less complex a code is the risk associated with maintaining, editing, or developing it is lowered. Cyclomatic complexity is still considered in modules on testing code validity today and remains relevant however I believe that the complexity of code cannot be measured simply. Complexity of code is determined by what is measured, this could be number of lines, readability, test coverage or even good variable naming. (Azzam, 2021) Cyclomatic complexity can be a positive measurement tool for code development, it could indicate that a function or module is too busy. On the other hand, in some cases code complexity is required for readability.
Overall, in an educational setting, using cyclomatic complexity to help new programmers to understand and keep in mind the complexity of a code is a positive trick however it shouldn’t be regarded as an end all compared to other testing tricks and tools out there.
Azzam A. (2021) Pros and Con of Cyclomatic Complexity as a Metric. Available from: https://medium.com/swlh/pros-and-cons-of-cyclomatic-complexity-as-a-metric-b25000dcda9c [Accessed: 05 September 2022]
IBM. (2021) Cyclomatic Complexity. Available from: ibm.com/docs/en/raa/6.1?topic=metrics-cyclomatic-complexity [Accessed: 05 September 2022]
MicroKernal Least-Privilege-Team response
In 2022, microkernel architectures offer superior stability and reliability to monolithic systems by modularising operating system processes (Foote, 2021; Fritzsch et al., 2019). However, Linus Torvalds rightly points out that an academically superior solution is useless when it is poorly developed, does not adhere to standards, and lacks community support (DiBona et al., 1999). Linux communities abound, and Linux has served as the underlying technology behind popular operating systems such as Android and ChromeOS due to its portability and ability to maximise system performance (Hoffman, 2017; Vaughan-Nichols, 2019). Linus Torvalds also acknowledges that the merits of system architectures reflect the technologies available (DiBone et al., 1999). With the era of quantum computing fast approaching, monolithic architectures may re-emerge as the best way to harness new-found computational power until another advancement enables better distribution of processing tasks; alternately, the inverse could also be true (Khan et al., 2022).
References
DiBona, C., Ockman, S., & Stone, M. (1999). Open Sources: Voices from the Open Source Revolution. [online] Available at: https://www.oreilly.com/openbook/opensources/book/appa.html. [Accessed 05 Sep 2022].
Foote, K.D. (2021). A Brief History of Microservices. [online] DATAVERSITY. Available at: https://www.dataversity.net/a-brief-history-of-microservices/ [Accessed 05 Sep 2022].
Fritzsch, J., Bogner, J., Zimmermann, A. and Wagner, S. (2019). From Monolith to Microservices: A Classification of Refactoring Approaches. Software Engineering Aspects of Continuous Development and New Paradigms of Software Production and Deployment, [online] pp.128–141. doi:10.1007/978-3-030-06019-0_10.
Hoffman, C. (2017). Android is Based on Linux, But What Does That Mean? [online] How-To Geek. Available at: https://www.howtogeek.com/189036/android-is-based-on-linux-but-what-does-that-mean/. [Accessed 05 Sep 2022].
Khan, A.A., Ahmad, A., Waseem, M., Liang, P., Fahmideh, M., Mikkonen, T. and Abrahamsson, P. (2022). Software Architecture for Quantum Computing Systems – A Systematic Review. SSRN Electronic Journal. doi:10.2139/ssrn.4040490.
Vaughan-Nichols, S.J. (2019). All Chromebooks will also be Linux laptops going forward. [online] ZDNet. Available at: https://www.zdnet.com/article/all-chromebooks-will-also-be-linux-laptops-going-forward/. [Accessed 05 Sep 2022].
